Heat-detecting cameras can help crack passwords up to a minute after typing them, researchers have found, as they warn similar systems could be developed by criminals to break into computers and smartphones.
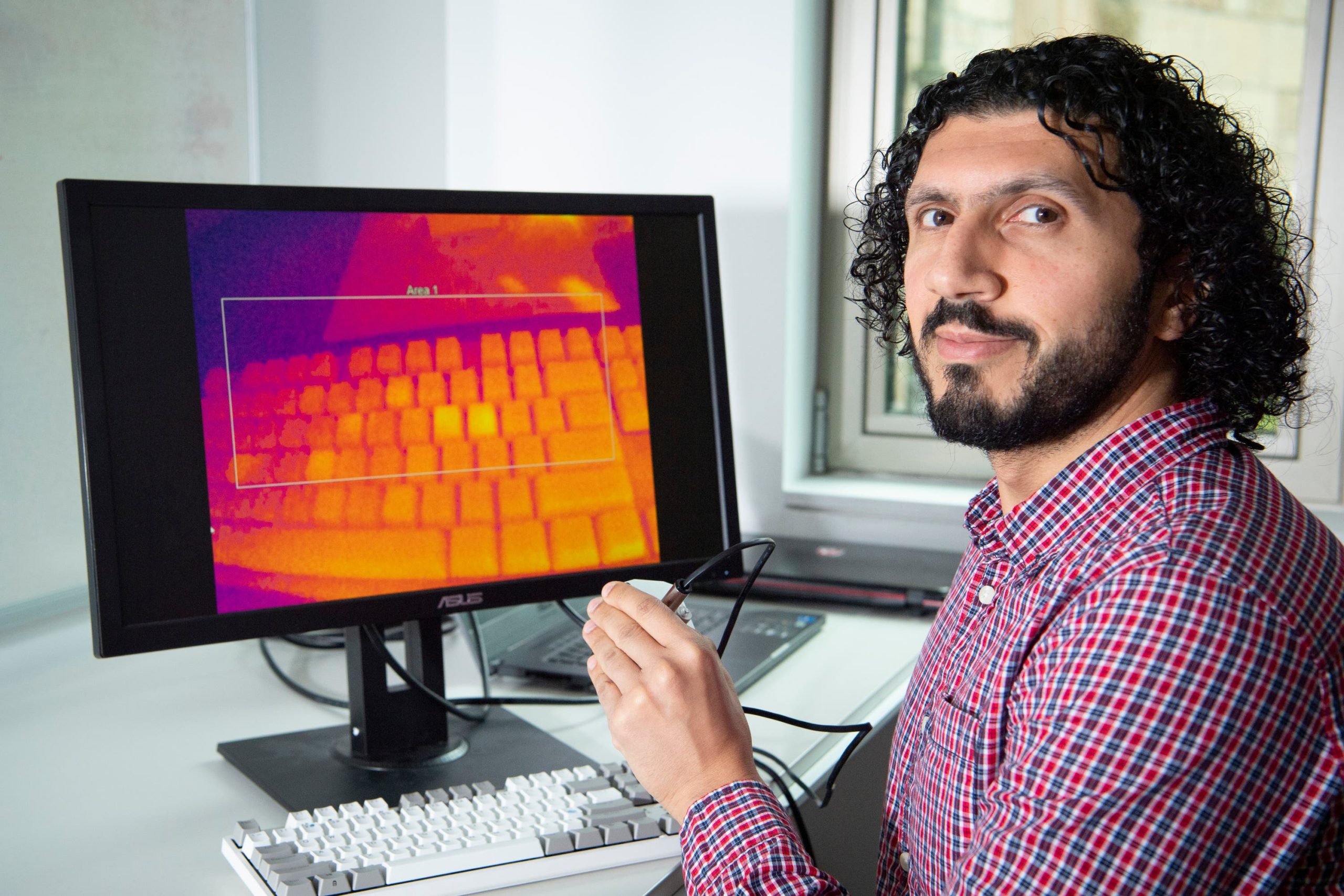
Heat from people’s fingertips can be detected on recently-used keyboards and, when thermal images were combined with the help of artificial intelligence, informed guesses of what the password could be were made by a tool developed by researchers at the University of Glasgow.
Some 86% of passwords were cracked when thermal images were taken within 20 seconds of typing in the secret code and put through their ThermoSecure system, and 76% when within 30 seconds. Success dropped to 62% after 60 seconds of entry.
They also found within 20 seconds, the system was capable of successfully attacking even long passwords of 16 characters, with a rate of up to 67% correct attempts.
As passwords grew shorter, success rates increased. Twelve-symbol passwords were guessed up to 82% of the time, eight-symbol passwords up to 93% of the time, and six-symbol passwords were successful in 100% of attempts.
Mohamed Khamis, of the Scottish university’s School of Computing Science, said: “They say you need to think like a thief to catch a thief.
“We developed ThermoSecure by thinking carefully about how malicious actors might exploit thermal images to break into computers and smartphones.”
In the images captured by the heat-detecting cameras, areas appear more bright the more recently they were touched.
Thermal attacks can occur after users type their password on a keyboard, smartphone screen or keypad, before leaving the device unguarded.
A passer-by equipped with a thermal camera can take a picture that reveals the heat signature of where their fingers have touched the device, with the brighter an area appears the more recently it had been touched.
By measuring the relative intensity of the warmer areas, researchers found, it was possible to determine the specific letters, numbers of symbols that make up the password and estimate the order in which they were used.
Dr Khamis, who led the development of the technology with Norah Alotaibi and John Williamson, said with thermal imaging cameras more affordable than ever and machine learning becoming more accessible, it was “very likely that people around the world are developing systems along similar lines to ThermoSecure in order to steal passwords”.
“It’s important that computer security research keeps pace with these developments to find new ways to mitigate risk, and we will continue to develop our technology to try to stay one step ahead of attackers,” he said.
The researchers, who published their findings in the journal ACM Transactions on Privacy and Security, also found how a user types affects the heat signature left on the keyboard, and therefore how easy it was to crack passwords.
“Hunt-and-peck” keyboard users who type slowly tend to leave their fingers on the keys for longer, creating heat signatures which last longer than faster touch-typists.
Meanwhile, the type of material keyboards are made from can affect their ability to absorb heat, with some plastics much more likely to retain a heat pattern than others.
Dr Khamis said longer passwords should be used wherever possible, with those more difficult to guess accurately.
“Backlit keyboards also produce more heat, making accurate thermal readings more challenging, so a backlit keyboard with PBT plastics could be inherently more secure,” he said.
“Finally, users can help make their devices and keyboards more secure by adopting alternative authentication methods, like fingerprint or facial recognition, which mitigate many of the risks of thermal attack.”